Adam Gowdiak (Founder/CEO, Security Explorations)
PRESENTATION TITLE: Security Threats in the World of Digital Satellite Television
PRESENTATION ABSTRACT:
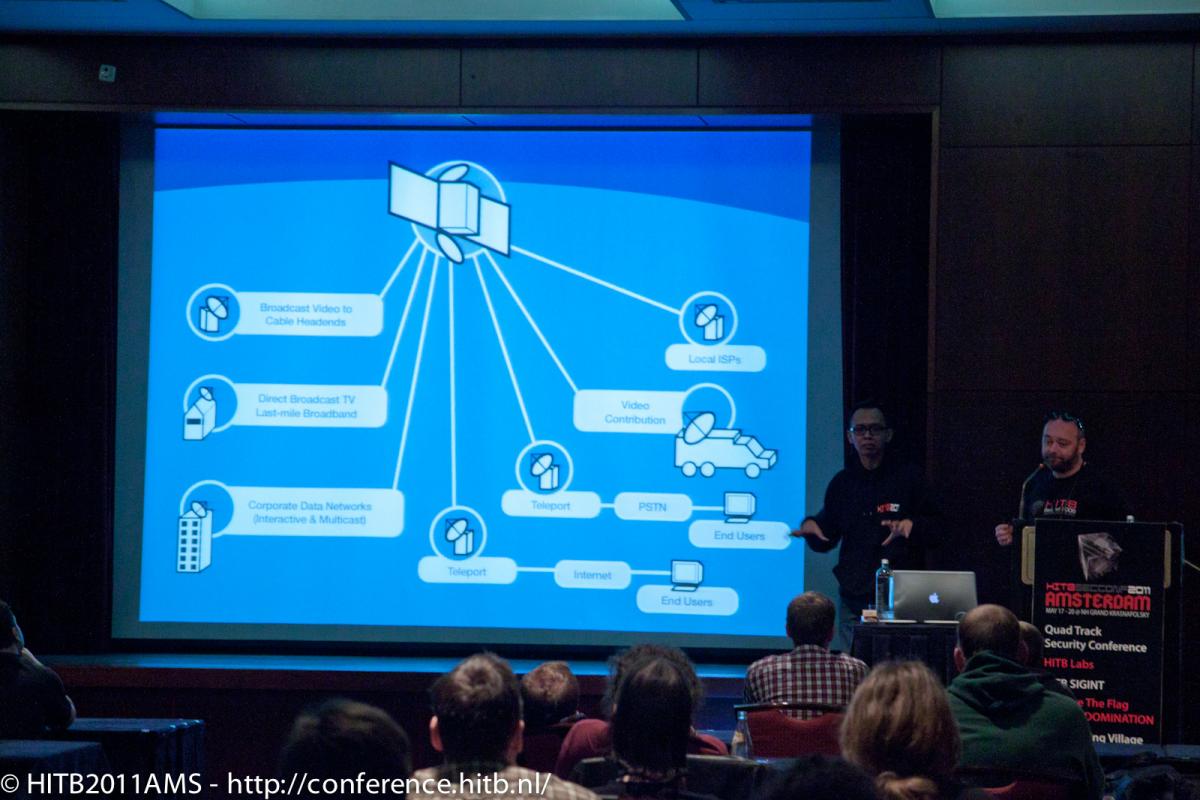
This presentation will showcase security threats in the context of the novel platform of digital satellite TV set-top-boxes. We will show that a combination of security issues present in software, hardware and services coming from different vendors can have a devastating impact on a security of the modern digital satellite TV platform.
The presentation will be divided into several parts. First, some brief information about the architecture of a modern digital satellite TV platform will be provided followed by a detailed discussion of a successful attack against Internet connected set-top-box devices allowing for the execution of arbitrary malware code on them. Information pertaining to the bypassing of a security of the OS and Java middleware atop of which the presented devices run, will be also given. Finally, details regarding persistent and stealth installation of backdoor / malware code on vulnerable set-top-boxes will be provided.
In addition to the above, technical details of about 20 security issues found in the environment of one of the biggest satellite TV operators in Poland (and potentially affecting other big satellite TV operators relying on the vulnerable equipment) will be given. Sample functionality of our 34,000 lines long Proof of Concept code will be also discussed for the purpose of illustrating the actual actions attackers / malware coders can take in the environment of a target set-top-box device.
This presentation will be followed up by an in-depth look at security vulnerabilities of Digital Video Broadcast chipsets. More information about the topic of this presentation can be found at: http://www.security-explorations.com/en/SE-2011-01.html
ABOUT ADAM GOWDIAK
Adam Gowdiak is the founder and CEO of Security Explorations, a security start-up company from Poland which provides various services in the area of security and vulnerability research.
Prior to founding Security Explorations, he worked for the Poznan Supercomputing and Networking Center and Sun Microsystems Laboratories. For over 8 years, he had been also an active member of a notable Polish security research group called the Last Stage of Delirium or LSD.
Adam is an experienced Java Virtual Machine hacker, with over 50 security issues uncovered in Java technology over the recent years. He is also the hacking contest co-winner and the man who has put Microsoft Windows to its knees (vide MS03-026) and was also the first one to present a successful and widespread attack against the mobile Java platform in 2004