

Early bird registration rate ends on the 30th of September
Cyber-criminals are innovating faster than ever, and the cybercrime industry caused the loss of hundreds of billions of dollars last year across the US and Europe alone. In this course, you will learn the skills you need to pull apart and analyze all forms of malicious software.
First, you will begin by exploring delivery techniques used by malware authors, such as office documents, spam and spear phishing. You will understand how malware is delivered and what happens next. This will also include pulling apart office document macros, PowerShell scripts and other techniques used to begin an attack on a system. You will learn how to identify obfuscation and effective ways for defeating it.
Next, you’ll work on unraveling the exploit kits–figuring out which ones were used, what they look like, how to decrypt them, and how to detect them in “the wild.”
Finally, you’ll learn how to conduct safe dynamic analysis, detect command and control (CNC) communication, and share your analyses so that these problems can be remedied. By the end of this course, you’ll not only have a deeper understanding of all stages of malicious software, but how to effectively analyze and share critical information.
Anyone wishing to dig into malware on a deeper level
How to pull real-world malware apart.
None- but some background in programming and architecture will be helpful.
A Windows virtual machine will be handed out on the first day of class via thumb drive, this will also contain all of the course material.
Students are required to provide a laptop for the course.
To use the virtual machine, you will also need to have installed virtualization software, such as VMWare Fusion, Workstation, Workstation Player or VirtualBox.
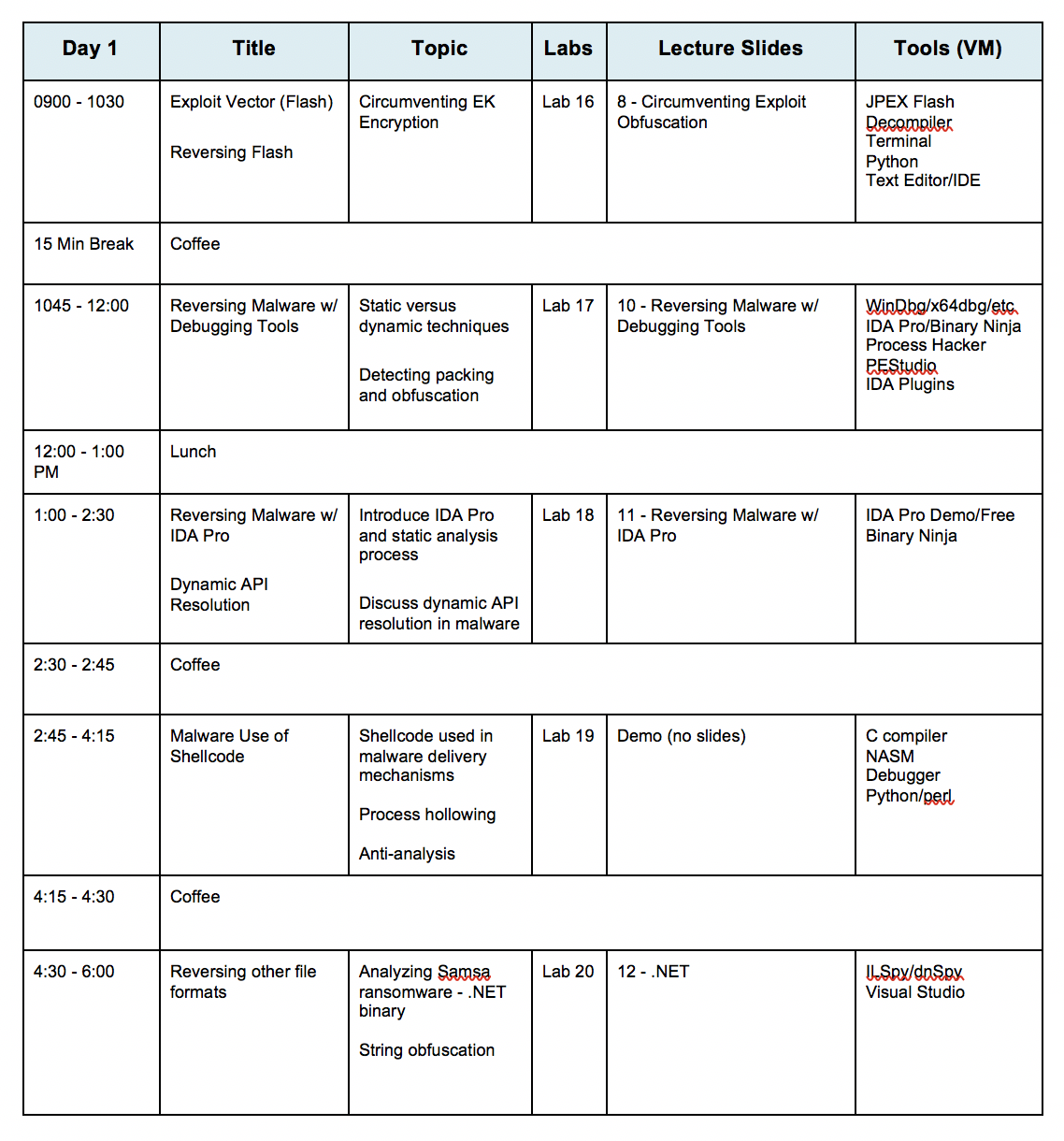
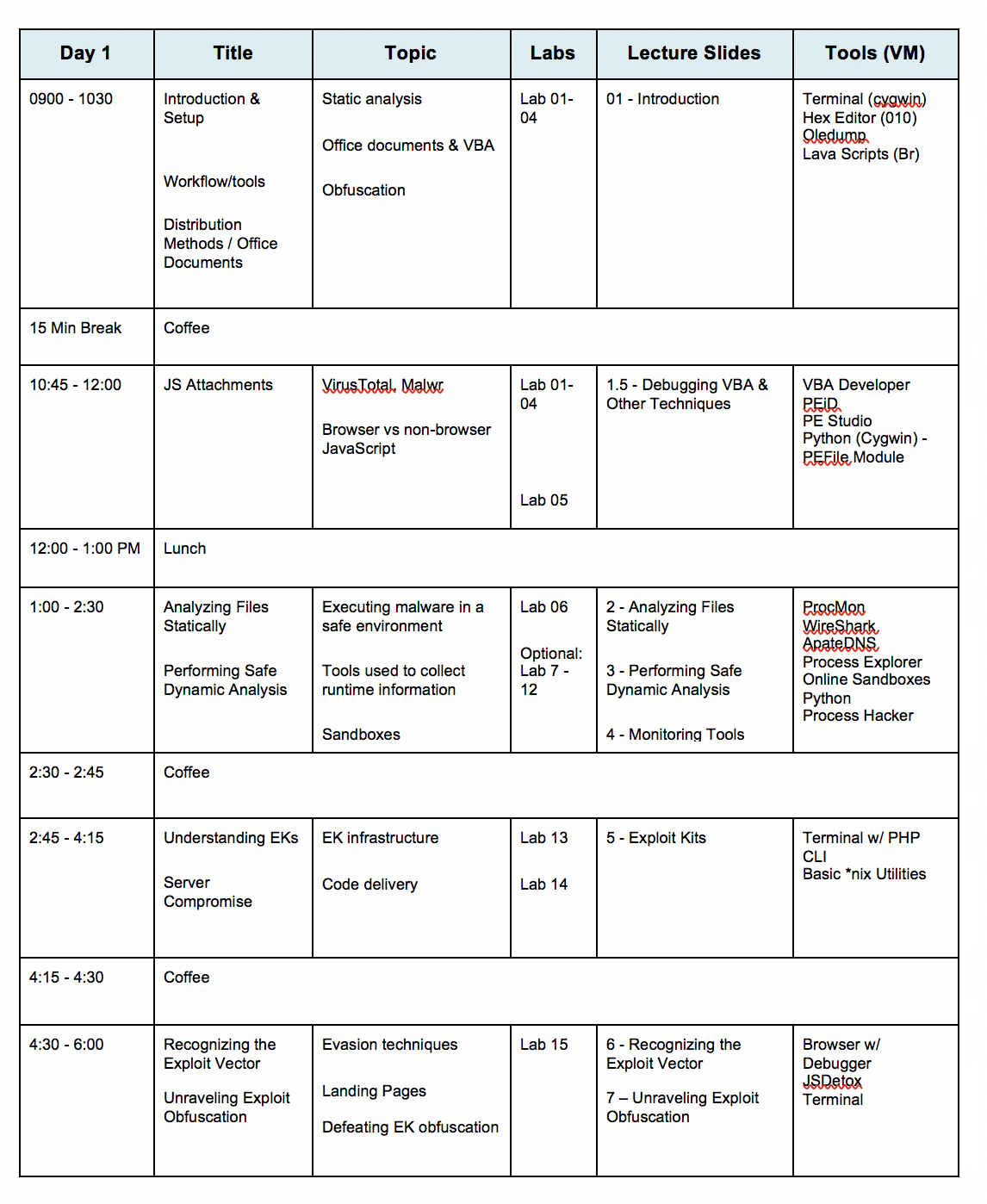
This course will move at a fast pace and assume that you have familiarization in basic malware analysis techniques, programming and scripting, and a variety of technologies. Any questions can be directed to training@vdalabs.com