THIS CLASS IS NOW BEING HELD ONLINE FOLLOWING SINGAPORE TIMEZONE (CET +6)
DURATION: 4 DAYS
CAPACITY: 15 pax
SEATS AVAILABLE: CLASS CANCELLED
USD3799*
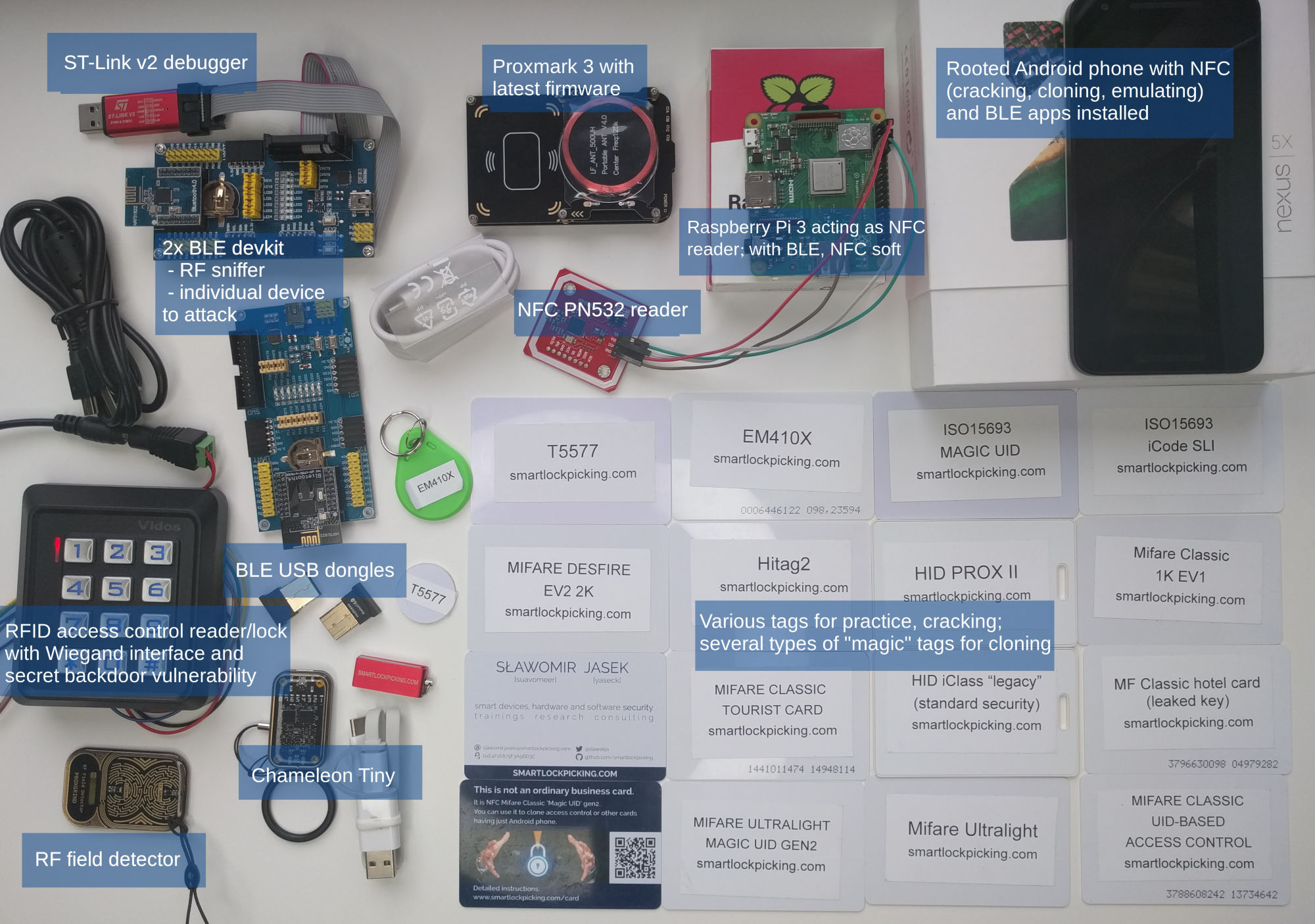
*The training has been updated for remote hands-on participation. Each attendee will receive a hardware pack worth over 300 USD shipped to you in advance (please register as soon as possible!). The hardware includes among others Proxmark 3, Chameleon Tiny, a rooted Android smartphone, BLE sniffer, BLE dedicated training device and Raspberry Pi (details below). With the specially arranged setup (simulated, working exactly like real NFC and BLE devices), participants will be able to perform hands-on practical exercises remotely – BLE analysis (sniffing, intercepting), cloning and cracking multiple kinds of proximity cards, analysing BLE or NFC mobile applications – not only during training but also any time later.
Overview
Bluetooth Low Energy is one of the most exploding IoT technologies. BLE devices surround us more and more – not only as recent COVID-19 spread prevention apps that utilize BLE for contact tracing, but also tons of wearables, toothbrushes, sex toys, smart locks, medical devices and banking tokens. Alarming vulnerabilities of these devices have been exposed multiple times recently. And yet, the knowledge on how to comprehesively assess their security seems very uncommon. This is probably the most exhaustive and up to date training regarding BLE security – for both pentesters and developers. Based on hands-on exercises with dedicated BLE training device flashed to a BLE devkit (working just like real device), and a deliberately vulnerable, training hackmelock.
RFID/NFC, on the other hand, has been around us for quite long. However, the vulnerabilities pointed out years ago, probably won’t be resolved in a near future. It is still surprisingly easy to clone most access control cards used today. Among other practical exercises performed on provided cards and simulated NFC devices, the attendees will reverse-engineer an example hotel access system, and as a result will be able to open all the doors in facility. A list of several hundred affected hotels included.
With prevalence of NFC smartphones, a new implementation of this technology is recently gaining attention: mobile contactless payments/access control, on Android known as Host Card Emulation. Using combination of cloud services and mobile security, it is now possible to embed not only credit card, but also NFC key to a lock in your phone. Is the technology as robust as advertised? How to check its security, and how to implement it correctly? Find out during practical exercises!
Previous Training Session Evaluation
Training score:
– Instructor: 90%
– Course material: 91%
Trainee’s Quotes
– Well prepared training, due to the amount of tools and equipment also easy to continue at home.
– Trainer did a good job in preparing all the labs. Really gorgeous.
– The best thing with this course is the instructor and our ability to do all exercise back at home .
– Great instructor, well maintained materials had a lot of experience.
– I am amazed how well everything is prepared.
– Great instructor, lot’s of information, topics and exercise to practise at home.
Who Should Attend
- Pentesters, security professionals, red teamers, researchers
- BLE/NFC device designers, developers
- Anyone interested
Key Learning Objectives
- In-depth knowledge of Bluetooth Low Energy, common implementation pitfalls, device assessment process and best practices for implementation
- Ability to identify vulnerable access control systems, clone cards and reverse-engineer data stored on card
Prerequisite Knowledge
- Basic familiarity with Linux command-line
- Scripting skills, pentesting experience, Android mobile applications security background will be an advantage but is not crucial
Hardware / Software Requirements
- Contemporary laptop capable of running Kali Linux in virtual machine (VirtualBox or VMWare), and at least two USB ports available for VM guest.
- Wifi to connect included Raspberry Pi
- Fast Internet (at least 30Mbps or better)
Each student will receive:
- Course materials in PDFs (over 2000 pages)
- All required additional files: source code, documentation, installation binaries, virtual machine images on a pendrive
- Included hardware pack of over 300 USD value for hands-on exercises, consisting of:
- Rooted NFC- and BLE-capable Android smartphone with all the required applications
- Proxmark3 with latest firmware
- Chameleon Tiny
- RF Field detector
- Multiple RFID/NFC tags for cracking and cloning, including “Chinese magic UID”, T5577, Ultralight, HID Prox, iClass, EV1, ISO15693, Mifare Classic with various content (bus ticket, hotel, e-wallet, …)
- NFC PN532 board (libnfc)
- Raspberry Pi (+microSD card and 3 A power adapter), with assessment tools and Hackmelock installed .
- 2x Bluetooth Low Energy development board: 1 acting as sniffer (nRF, Btlejack), 1 as dedicated BLE device to interact and attack
- ST-Link V2 SWD debugger for programming nRF boards
- 2 x Bluetooth Low Energy USB dongles
- Sample RFID access control reader/lock with Wiegand interface and secret backdoor vulnerability
Agenda – Day 1
Bluetooth Smart (Low Energy)
- Theory introduction
- What is Bluetooth Smart/Low Energy/4.0, how it is different from previous Bluetooth versions?
- Usage scenarios, prevalence in IoT devices
- Protocol basics
- required hardware for BLE assessment
- BLE advertisements
- Scanning for visible devices – mobile applications, hcitool, bleah, bettercap, Mirage, GATTacker, …
- Beacons: iBeacon, Eddystone, Physical Web
- Simulating beacons – using mobile phone, Linux scripts, other devices.
- How to get free beer by abusing beacon-based reward application
- Smart underwear using beacons
- “Encrypted” beacons, abusing weaknesses in beacon management control protocols
- Coronavirus spread-prevention contact tracing mobile applications
- BLE advertisements of Microsoft and Apple devices (user tracking, decoding of current status/phone number)
- Advertisement spoofing – Denial of Service, device impersonation
- BLE connections
- Central vs peripheral device
- GATT – services, characteristics, descriptors, handles, reading, writing, notifications
- Mapping device services and characteristics
- Interacting with BLE devices using mobile phone, command-line, various tools
- Taking control of simple, insecure devices – sex toys, key finders, …
- Sniffing BLE connections using RF layer hardware
- BLE radio modulation, channels, hopping, connection initiation
- BLE link layer encryption – introduction, why is it hardly used in practice
- Sniffing hardware: Ubertooth, nRF sniffer, BtleJack, Sniffle, SDR …
- Practical sniffing of BLE communication between mobile app and your dedicated training device
- Wireshark filters, tips&tricks
- Sniffing static cleartext password of a smart lock and other devices
- HCI dump – capturing own BLE traffic
- Difference from RF layer sniffing
- Linux command-line hcidump
- Android: live BLE packets analysis in Wireshark via TCP service
Agenda – Day 2 – BLE continued
- Device spoofing, active MITM interception
- How to perform “man in the middle” attack on BLE connections
- Available tools: GATTacker, BtleJuice, BtleJack, Mirage
- MAC address cloning, mobile OS GATT cache potential problems
- Analysing intercepted traffic
- Denial of Service attacks
- Jamming and hijacking active connections with BtleJack
- Replay attacks
- Intercept transmission
- Analyse authentication protocol weakness in example smart lock
- Perform replay using tools or mobile phone, and unlock the device
- Relay attacks – abusing automatic proximity features (e.g. smart lock autounlock).
- Various smart locks vulnerabilities case-studies
- Attacks on proprietary authentication and protocols
- Decompile Android app, locate relevant source code fragments
- Understand proprietary BLE communication protocol – commands, data exchanged with device
- Based on example smart lock, discover protocol weakness, create exploit to open the lock without knowing current password or prior sniffing
- Exploit the vulnerability using just a mobile phone – nRF Connect macros
- Verify other vendor’s claims on “Latest PKI technology” and “military grade encryption”
- Example unlocked AT command interface via BLE service of a smart lock
- Remote access share functions and their weaknesses – how to bypass timing restrictions.
- How to create own, independent server-side API for device – based on a real smart lock vendor, which disappeared and shut the servers, effectively rendering the device e-waste
- Device DFU firmware update OTA services and their vulnerabilities.
- Bluetooth link-layer encrypted connections
- BLE pairing, bonding, encryption
- Intercepting pairing process and decoding Long Term Keys (crackLE)
- Weaknesses of simple pairing (static PIN, just works)
- How to trick a victim into re-pairing
- Abusing BLE bonding trust relationships
- Analysis of Google Titan U2F token vulnerability
- Possibilities for malicious actions (e.g. change device to appear as a BLE keyboard).
- Web Bluetooth – interfacing with nearby devices from javascript.
- How hard is it to hijack BLE devices from a hostile web site
- Writing new javascript interface to control own device
- Bluetooth Mesh, Bluetooth 5.0 – what these technologies change and what not in terms of BLE security.
- BLE Hackmelock – open-source software emulated device with multiple challenges to practice at home.
- BLE best practices and security checklist – for security professionals, pentesters, vendors and developers.
Agenda – Day 3 – RFID/NFC
- Short introduction
- RFID/NFC – where do I start?
- Frequencies, card types, usage scenarios
- How to recognize card type – quick walkthrough
- Equipment, and what can you do with it – mobile phone, card reader, simple boards, Chameleon Mini/Tiny, Proxmark, other hardware
- UID-based access control
- UID-based access control – still surprisingly popular
- UID lengths, formats
- Clone Mifare UID using Android phone and “gen2” UID-changeable card, or libnfc/Proxmark and gen1 card
- How to emulate contactless cards and unlock UID-based system using just a smartphone (Android, iOS), without any additional hardware
- How to clone a card by making its picture – decoding numbers printed on cards
- Cloning other ID-based cards – Low Frequency EM41XX, HID Prox, …
- Emulate card using Proxmark, Chameleon Mini
- Brute-force – is it possible in practice to guess other cards UID?
- Countermeasures against attacks
- Wiegand – wired access control transmission standard
- Sniff the data transmitted from access control reader using Raspberry Pi GPIO, ESP RFID Tool, BLE-Key, …
- Decode card UID from sniffed bytes, clone the card
- Replay card data on the wire to open lock
- Mifare Ultralight
- Data structure
- Reading, cloning, emulating
- Example data stored on hotel access card
- Ultralight EV1, C
- Mifare Classic & its weaknesses – practical exercises based on hotel door lock system, ski lift card, bus ticket
- Mifare Classic – data structure, access control, keys, encryption
- Default & leaked keys
- Reading & cloning card data using just a mobile phone
- Cracking keys – nested, darkside attacks
- Libnfc tools – mfoc, mfcuk, MiLazyCracker
- Cracking Mifare using Proxmark
- Attacks on EV1 “hardened” Mifare Classic
- Online attacks against reader
Agenda – Day 4 – RFID/NFC Continued
- Reverse-engineering data stored on card – based on a real hotel system
- Recoding access control data (room number, date) stored on card by an example hotel system
- Creating hotel „emergency card” to open all the hotel doors unconditionally
- Mifare DESFire – introduction, sample attack on misconfigured access control system, attacks on city cards
- ISO15693/iCode SLIX
- Cloning ISO15693 UID on a “magic UID” card, unlocking smart lock
- Data of several example ski passes
- HID iClass
- Cloning “legacy” / “standard security” iClass
- Attacks on iClass Elite
- Hitag2 access control
- Sniffing password mode transmission between reader and tag
- Simulating Hitag2 against the reader using Proxmark
- Intercepting card data from distance – building antenna, possibilities and limits.
Host Card Emulation – phone acting as NFC
- Hardware Secure Element vs software Host Card Emulation
- Practical exercises with example vulnerable HCE access control system (unlocking door using your NFC phone) simulated on included Raspberry Pi with attached NFC board
- Protocols, commands, applications – ISO14443-4, 7816-4, APDU, AID, …
- Analysis, sniffing NFC using Proxmark, dumping NFC on the phone,
- Bypassing security mechanisms, key extraction, spoofing other user’s credentials
- Remote relay attacks and countermeasures


