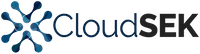$4,299.00
| Date | Day | Time | Duration |
| 30 Aug | Tuesday | 10:00 to 18:00 PDT/GMT-7 | 8 Hours – Presentations & Hands-on exercises |
| 31 Aug | Wednesday | 10:00 to 18:00 PDT/GMT-7 | 8 Hours – Presentations & Hands-on exercises |
| 01 Sept | Thursday | 10:00 to 18:00 PDT/GMT-7 | 8 Hours – Presentations & Hands-on exercises |
| 02 Sept | Friday | 10:00 to 18:00 PDT/GMT-7 | 8 Hours – Presentations & Hands-on exercises |
Through an applied understanding of introductory program analysis and binary translation, techniques for finding various bug classes and methods for improved crash debugging will be discussed. We will take a deep dive into fuzzing, covering all aspects of this practical approach to finding bugs. As the most approachable and versatile of the available tools, the student will apply various fuzzing techniques to several real-world pieces of software. Students will learn strategies for analyzing attack surface, writing grammars, and generating effective corpus. We will explore in detail the latest innovations such as harnessing code coverage for guided evolutionary fuzzing and symbolic reasoning for concolic fuzzing.
We approach crash analysis through the lens of scriptable debuggers and program analysis. We will apply tools like reverse debugging and memory debuggers to assist in interactively diagnosing root cause of crashes. Then we will leverage the power of dynamic taint tracking and graph slicing to help isolate the path of user controlled input in the program and identify the exact input bytes influencing a crash. Lastly, we will look at possible ways to determine the impact of a vulnerability.
This class will focus on x86/x64 architecture and target file parsers, network parsers and browsers on both Windows and Linux environments.
Mr. Gal Diskin is a cybersecurity and AI researcher. He was previously the VP & head of Palo Alto Networks’ Israeli site, and is a serial entrepreneur. Mr. Diskin’s research has been featured in HITB, Defcon, Black Hat, CCC, and other conferences, spanning fields from low level security research such as hardware vulnerabilities, binary instrumentation, and car hacking to high level research on AI detection methods, Enterprise security, and Identity security. Mr. Diskin was also the technical lead and co-founder of Intel’s software security organization, as well as the CTO of Cyvera and HeXponent (co-founder) before their acquisition.
Huajiang “Kevin2600” Chen (Twitter: @kevin2600) is a senior security researcher. He mainly focuses on vulnerability research in wireless and Vehicle security. He is a winner of GeekPwn 2020 and also made to the Tesla hall of fame 2021. Kevin2600 has spoken at various conferences including KCON; DEFCON and CANSECWEST.
intercontinental singapore

follow us