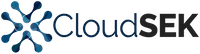$4,299.00
| Date | Day | Time | Duration |
| 22 Aug | Monday | 0900-17:00 SGT/GMT +8 | 8 Hours – Presentations & Hands-on exercises |
| 23 Aug | Tuesday | 0900-17:00 SGT/GMT +8 | 8 Hours – Presentations & Hands-on exercises |
| 24 Aug | Wednesday | 0900-17:00 SGT/GMT +8 | 8 Hours – Presentations & Hands-on exercises |
| 25 Aug | Thursday | 0900-17:00 SGT/GMT +8 | 8 Hours – Presentations & Hands-on exercises |
The TEEPwn experience provides an offensive system-level perspective and dives into the darker corners of TEE Security. It is designed with a system-level approach, where you will experience powerful exploitation of TEE vulnerabilities. The TEEPwn experience is hands-on, gamified and driven by an exciting jeopardy-style Capture the Flag (CTF).
Your journey starts by achieving a comprehensive understanding of TEEs, where you will learn how hardware and software concur to enforce effective security boundaries. You will then use this understanding for identifying interesting vulnerabilities across the entire TEE attack surface. You will then be challenged along the path to exploit them in multiple scenarios. All vulnerabilities are identified and exploited on our emulated attack platform which implements an ARMv8 (64-bit) TEE based on ARM TrustZone.
You will take on different roles, as an attacker in control of:
TEEPwn will guide you into an unexpected range of attack vectors and TEE-specific exploitation techniques, which may be leveraged for novel and creative software exploits. refining your skills to a new level.
Deliverables
During the training we will provide you with the following:
We will also provide you the following in order to continue with the exercises after the training:
Format
This TEEPwn experience will be given in a hybrid format where attendees are able to join in-person and online at the same time. Attendees need to select the desired format before the start of the training.
Topics Covered
Mr. Gal Diskin is a cybersecurity and AI researcher. He was previously the VP & head of Palo Alto Networks’ Israeli site, and is a serial entrepreneur. Mr. Diskin’s research has been featured in HITB, Defcon, Black Hat, CCC, and other conferences, spanning fields from low level security research such as hardware vulnerabilities, binary instrumentation, and car hacking to high level research on AI detection methods, Enterprise security, and Identity security. Mr. Diskin was also the technical lead and co-founder of Intel’s software security organization, as well as the CTO of Cyvera and HeXponent (co-founder) before their acquisition.
Huajiang “Kevin2600” Chen (Twitter: @kevin2600) is a senior security researcher. He mainly focuses on vulnerability research in wireless and Vehicle security. He is a winner of GeekPwn 2020 and also made to the Tesla hall of fame 2021. Kevin2600 has spoken at various conferences including KCON; DEFCON and CANSECWEST.
1. Stable Internet connection with sufficient bandwidth
2. Any modern computer system or laptop:
intercontinental singapore

follow us