








What is the HITB CommSec Village
A free-for-public showcase area which features exhibits and workshops by the security communities, open source groups, enterprise bodies and technology companies. Come check out latest projects, gadgets and toys. Or get involved in some hands-on workshops, soldering and tinkering at the hardware, soldering, or lock picking villages. And of course, do be sure to check out the highly-popular HITB Capture The Flag competition which will run here across both exhibition days.
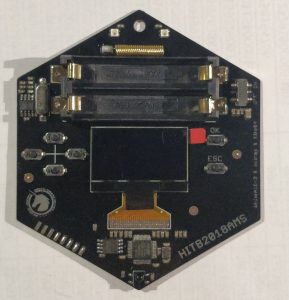
All registered conference attendees will get their own HITBSecConf2018 – Amsterdam badge exclusively designed by the Qihoo360 Unicorn Team!
Come by the badge village to unlock secret badge features, mini games and more! We’ll also show you how to get started reprogramming the badge and hacking it to do more stuff!
What’s On the Badge?
The badge is fully open sourced (both the hardware and software will be provided along with the firmware for the badge).
Hardware Specs:
In addition, limited quantities of the UnicornCUBE / HackCUBE will also be available for purchase and for pre-order. Copies of the newly released Inside Radio: An Attack and Defense Guide will also be available for you to pick up.
Organized by the team of ninja’s at Quarkslab, this CTF will involve hardware-oriented challenges. Be prepared to deal with various tasks involving RF protocols, RFID, automotive, soldering, micro-soldering, side-channels, etc.
To register (as an individual or as a team), please come by our challenge area. We provide all the require tools to solve the challenges, you will just need a laptop to solve some of them. Note that Linux is typically easier to work with than Windows when it comes to compiling tools, dealing with drivers etc.
The CTF is jeopardy style: you’ll get points when you solve challenges. The first three winners will be rewarded with some nice tools sponsored by WhiteMotion.
Join this reverse engineering and exploitation contest and stand a chance to win a trip to Hong Kong to attend the beVX conference in September! Participants will need to reverse engineer and write an exploit a vulnerability in an ARM binary. The first person to submit a complete solution will get a round trip flight and accommodation and entrance to beVX conference in September in HK, second place gets flight and entrance, and the third place gets an entrance ticket to the event.
The link to the download page and game instructions will be provided on-site during the 12th and 13th. The challenge binary will be internet accessible and downloadable on-site – you do not need to sit at our booth to solve it.
If you can hack it here, you can hack it everywhere! Developed by Applied Risk ICS/SCADA security experts, join our SCADA Capture the Flag challenge at the 9th annual HITB Security Conference to be in with the chance of winning prices. The winners of the challenge will have to successfully discover and report all known and unknown vulnerabilities within our test environments.
Do you think you have the expertise to spot a security flaw? Our SCADA Capture the Flag challenge will take plac eover two days at the event on 12th -13th April, providing those that take part with the knowledge and skills to successfully identify and report potential threats in real SCADA environments. We look forward to testing your SCADA security knowledge!
Want to tinker with locks and tools the likes of which you’ve only seen in movies featuring police, spies, and secret agents? Then come on by the Lockpick Village, run by The Open Organisation Of Lockpickers, where you will have the opportunity to learn hands-on how the fundamental hardware of physical security operates and how it can be compromised.
The Lockpick Village is a physical security demonstration and participation area. Visitors can learn about the vulnerabilities of various locking devices, techniques used to exploit these vulnerabilities, and practice on locks of various levels of difficultly to try it themselves.
Experts will be on hand to demonstrate and plenty of trial locks, pick tools, and other devices will be available for you to handle. By exploring the faults and flaws in many popular lock designs, you can not only learn about the fun hobby of sportpicking, but also gain a much stronger knowledge about the best methods and practices for protecting your own property.
Mitch is a hacker and inventor, most well known for inventing TV-B-Gone, he’s been a speaker at numerous hacker conferences, is an international expert on the hackerspace movement and teaches introductory electronics workshops. He has already taught over 50.000 people how to solder – from 3 year olds to grandmothers! Here’s your chance to learn how to solder one of Mitch’s electronic kits including the TV-B-Gone, Trippy RGB Waves, The Brain Machine but also all types of Arduinos and accessories!




Beyond Security’s SecuriTeam Secure Disclosure (SSD) can help you turn your experience uncovering security vulnerabilities into a highly paid career. SSD was designed by researchers for researchers and will give you the fast response and great support you need to make top dollar for your discoveries. We work with some of the brightest and most highly compensated people in the security industry and can help you advance your game – regardless of whether you are a beginner or have been discovering security issues for years.
DarkMatter is transforming the cyber security landscape. Headquartered in the United Arab Emirates and operating globally, it is the region’s first and only fully integrated digital defence and cyber security entity developing, delivering and implementing next-generation cyber security capabilities.
Our elite team of global experts deliver advanced, next-generation solutions to governments, enterprise, and other entities with the highest cyber security requirements. Innovation and Research underpin everything we do, and our vision is to “protect the future by securing its technologies.
Nixu provides cybersecurity consultancy and –services to help organizations identify and mitigate the risks of digitally connecting people, information, production, business and devices whilst complying with the applicable regulations.
Our consultants offer their unique knowledge and international experience to customers in nearly every industry, and share their newly acquired knowledge and insights –as far as confidentiality permits- with the global community of cyber security professionals that Nixu is a part of.
Information Security Engineering is a global organization responsible for Product Security and all-around hacking: breaking and fixing Google’s code, providing security reviews and advice to engineers working on thousands of different projects, working with third-party vendors to help Google outsource business functions securely, and carrying out cutting-edge security research. Our mission is to keep Google’s millions of users safe and secure.
We work on a stunning array of different technologies: everything from hardware up through the software stack, including numerous different languages and frameworks. The organization is made up of various sub teams or focus areas: API and framework Hardening, Red Team, Security Education, Security Test Engineering, Third Party Security, and Security Reviews.
We are part of the broader software engineering organization at Google, and work closely with other engineers to help them produce more secure code. We perform security reviews for thousands of product launches every year. In addition, the ISE Red Team handles a large volume of Third Party Vendor and Acquisition reviews annually. We also work on diverse software engineering projects, from creating robust sandboxes for untrusted code, Web application scanning and testing tools, through fuzzers, or tools for detecting attacks.
CloudSek is an artificial intelligence technology-based threat intelligence enterprise, which focuses on customized, intelligent threat monitors.
Peerlyst is the place where information security pros go to share knowledge and build their professional reputations. With an audience of more than half a million, Peerlyst is the preeminent platform for spreading InfoSec news, asking a question, finding an expert, or offering product insight.
null – the open security community is a registered non-profit society in India. The objective of null is to spread security awareness, knowledge and assist government, private organizations with cyber security issues. We are an active community of information security professionals in Asia consisting of 11 chapters throughout India – Delhi, Chandigarh, Kolkata, Mumbai, Bangalore, Hyderabad, Pune, Chennai, Dharamsala, Ahmedabad and Bhopal and Three abroad – Amsterdam, Dubai and Singapore where we organize free monthly meets and workshops to share technical knowledge on security.
null community is open, professional, inclusive, responsible and most importantly completely vounteer driven. We also run the most sought after security jobs portal – null Jobs (https://jobs.null.co.in), which is a free service for both job seekers and recruiters. We are a fun community to hangout with, come visit us to:
1. Tickle your grey cells and solve hardware puzzles
2. Volunteer to speak/present at our monthly null Chapters meets
3. Join us for our Human Code Scanner challenges and WIN Goodies