THIS CLASS IS NOW BEING HELD ONLINE FOLLOWING SINGAPORE TIMEZONE (CET +6)
DURATION: 3 DAYS
CAPACITY: 15 pax
SEATS AVAILABLE: CLASS CANCELLED
USD2599
Overview
Discover the world of Industrial Control Systems with an attack mindset! In this 3-day training, we will follow a hands-on approach, growing from a very simple local process to a realistic ICS environment with 3 words in mind:
- Build: how does it work?
- Break: what are the weaknesses and how to exploit it?
- Secure: what can we do to fix it?
You will perform a lot of lab sessions, including: programming a PLC in ladder logic, analyzing network captures of ICS protocols, perform Modbus requests, using Metasploit to compromise a Windows host and gather sensitive information from an Active Directory, and much more! The last half-day is dedicated to the Capture-the-Flag, in which you will apply the newly acquired techniques to compromise a corporate network, pivot to the ICS network and take control of the process to capture a flag with a robotic arm.
Moreover, the training doesn’t stop on the third day! With the WhiskICS virtual training kit, you’ll be able to redo all the exercises after the training and continue experimenting with ICS security on your own.
COVID-19 updates
In order to be able to give the training remotely, the following adjustments have been/will be made to the training:
- Training kit: as it is difficult to source components at the moment, and it will be difficult to ship hardware kits to all students, no hardware kit will be provided to students. However, all planned exercises will be performed on a virtual kit, as described in The WhiskICS student virtual kit.
- CTF: One of the most appreciated part of the training is the final CTF that allows to perform a full attack on an ICS network, from compromising an Active Directory environment to messing with a model train. This CTF has been migrated to the Cloud. A dedicated server is rented (16 CPU cores, 128GB RAM, 2TO NVME SSD) to host all the CTF machines. A VPN access is provided to all students. In order to replace the real PLCs used in the training, either simple simulators are used or full-fledge PLC simulator as embedded into SCADA software (soMachine, Codesys) so the attacks will work as if they were performed on real hardware. Since there is no “physical” display of the process to hack, an HTML5 webapp was developed to simulate the physical process. This webapp is connected to the PLCs and allows participants to observe the effectiveness of the attacks:
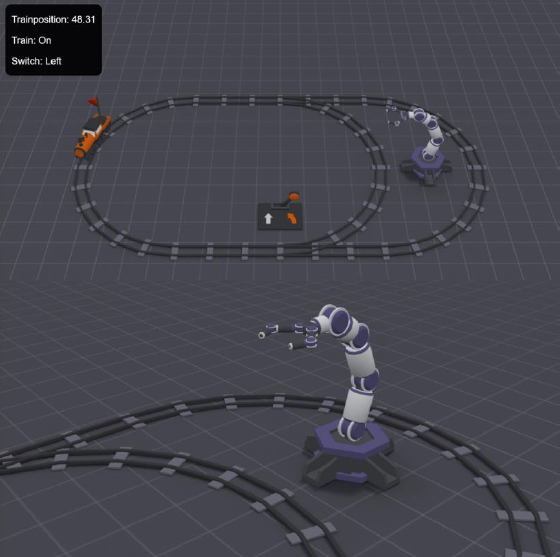
- Elearning platform: In addition to the live training, each participant will get a 30-day access to both the CTF platform and a new elearning portal. The elearning portal will contain video recordings of all training content, as well as some exercises. So the participants will be able to redo all exercises, watch all the content during 30 days.
Key Learning Objectives
-
Understand Industrial Control Systems by DOING (programming a PLC, using ICS protocols, programming a SCADA)
-
Have a realistic CTF event the last afternoon to perform pentest on Windows AD, pivot to the ICS network, and hack the PLCs
-
Give a realistic vision of ICS, not only technical, that will allow attendees to work closely with ICS teams by having a common understanding and vocabulary
Who Should Attend
This training aims at bridging the gap between IT and ICS: it is designed to allow OT professionals to understand the security challenges of ICS with an offensive mindset, while allowing IT professionals to discover the world of Industrial Control Systems and adapt their cybersecurity knowledge to this new world.
Prerequisite Knowledge
The training is heavily hands-on. While no ICS or pentest knowledge is required, it is recommended for attendees to have basic networking and computers skills (using virtual machines, the command line, understanding TCP/IP, etc.)
Hardware / Software Requirements
- Attendees need to bring a laptop with Virtualbox, capable of running 64-bits virtual machines
- 8GB RAM & 50GB free disk space recommended
*The WhiskICS Student virtual Kit
The WhiskICS student kit is a software kit that allows attendees to create their own simple ICS, attack it and secure it. At the core of WhiskICS are 3 main components:
- An HTML5 webapp that simulates the physical process and allows participants to have visual feedback on the process
- A Codesys soft-PLC: On a provided Windows VM, the Codesys IDE will be installed and will allow participant to program a “soft” PLC which is a PLC running on standar hardware. This will also allow them to program a virtual HMI, to graphically control the PLC
- Schneider IGSS software will also be used on the VM to act as the SCADA software, allowing to remotely supervise and control the physical process
As the name suggests, WhiskICS simulates a (very simplified) process of distillation, used in the whisky making process. Attendees will need to control valves, a heater and condenser to fill a whisky barrel; they will also perform attacks to impact the process reliability and quality.
Agenda – Day 1:
[BUILD] Introduction to ICS
- A brief history of ICS
- Vocabulary
- The CIM model
- Classic architectures
- ICS components (PLCs, HMI, SCADA, DCS, sensors, RTUs, Historian, etc) and their roles OT vs IT
[BUILD] Introduction to the case study and the WhiskICS student kit
- Short introduction to whisky making
- Different steps and focus on distillation
- Technical presentation of the WhiskICS student kit
[BUILD] Automation Basics & programming PLC
- Introduction to automation (PID loop…)
- Basic steps of programming a PLC
- LAB: programming several examples on the student kit with Codesys IDE
[BUILD/BREAK] ICS protocols
- General presentation of ICS protocols (fieldbus, supervision, data exchange)
- LAB: exercises on analysis of network packet capture (modbus/tcp, OPC-UA)
- LAB: Exchange data with the student kit PLC using modbus clients (serial & tcp) as well as OPC-UA client
[BREAK] Hacking the process
- Short discussion on the difficulties of hacking a real process and presentation of research work on the topic (“easy button for cyber-physical ICS attacks” by Reid Wightman, “Rocking the pocket book: hacking chem plants” by Marina Krotofil and Jason Larsen).
[BREAK] Attacking the non-ICS part of the PLC
- Presentation of PLCs internal architecture
- Discussion about OS and middleware (codesys)
- Presentation of vulnerabilities on standard interfaces (web, ftp, snmp…)
- LAB: Identify & exploit exposed interfaces on the student kit PLC
[BREAK] PLC proprietary protocols
- Presentation of Modbus 90 function used by Schneider PLCs
- LAB: Use of specific exploits against Schneider simulators
[SECURE] An introduction to safety
- Presentation of layers of safety, including SIS, physical safety…
- Presentation of safety analysis methods and link to cybersecurity (SPR: Security PHA review)
- LAB: Performing a SPR on a simplified HAZOP analysis of the distillation process
Agenda – Day 2:
[BUILD] Process supervision: SCADA and DCS
- General presentation on supervision systems (SCADA & DCS)
- LAB: Programming a SCADA software to interact with the WhiskICS student kit
[BREAK] Linking to corporate environments: Windows & Active Directory security
- Presentation of Windows
- Introduction to Active Directory
- Credential management in Active Directory (NTLM, Kerberos..)
- LAB: Exploiting a Windows vulnerability with Metasploit
- LAB: Gathering credentials and pivoting to other systems
- LAB: Gathering information from Active Directory (users, computers…)
[BREAK] SCADA/DCS specific vulnerabilities
- Description of common DCS/SCADA vulnerabilities
- LAB: Gathering interesting data from SCADA project files
[BUILD] Industry 4.0 & IIoT
- Industry 4.0 genesis & use cases
- Industry 4.0 technologies
- Industry 4.0 & IIot communications protocols (LoRa, Sigfox, MQTT…)
- LAB: Analysis of a MQTT network capture
- LAB: MQTT pentest
[SECURE] ICS cybersecurity general approach
- Leading ICS cybersecurity standards (NIST, IEC62443)
- Open discussions on how to get it done!
Agenda – Day 3:
[SECURE] Data exchange between ICS and the outside world
[BREAK] ICS security assessments
[BREAK] CTF


