




The top 3 teams from this pre-qualifer round will qualify to play the PRO CTF FINALS @ HITB+ CYBERWEEK in Abu Dhabi in person (The finals are to take place in a dual game format in-person and online from November 24 – 25th at the Abu Dhabi National Convention Center). Other top-ranked teams from this prequalifer EDU CTF will also be invited to participate in the PRO CTF Finals @ HITB+ CyberWeek but only online. (Note: Educational establishment affiliation documents will be required and checked for EDU participants of the HITB+ CyberWeek PRO CTF Finals)
30th July – Pre-qualification CTF registration opens
13th August – Last day for registration to the pre-CTF online training session
14th & 15th August – Online Training Session for all teams who registered before the 13th.
26th August – Passwords to the cloud infrastructure will be sent to team captains
27th August @ 18:00 SGT (UTC+8) – Cloud infrastructure boot up
27th August @ 19:00 SGT (UTC +8) – Network is open, Hack on!
28th August @ 05:00 SGT (UTC +8) – GAME ENDS
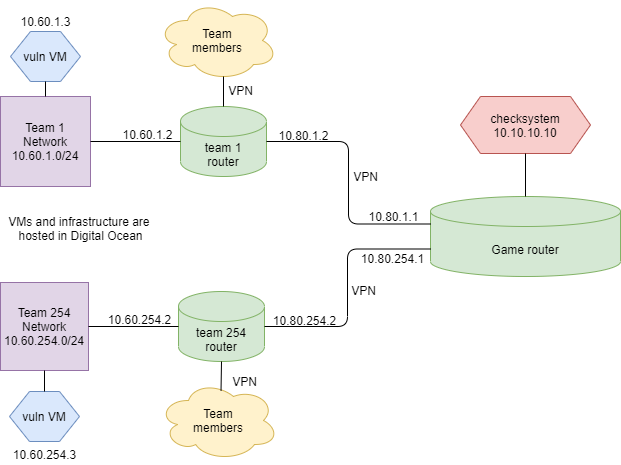
At the start teams get identical virtual servers with a set of vulnerable services. Teams’ goal is to find the vulnerabilities, fix them in their services and use them to get private info (flags) from other teams’ services. The game is continuously monitored by an independent checksystem, which regularly puts new flags on teams’ services and also receives flag submissions from teams.
It is difficult to give a complete set of rules for a CTF challenge, so these rules can change without notice at any moment prior to game start. That is why we recommend checking the rules one more time before the competition starts. Just in case 🙂
A group of people with a captain.
A vulnerable application written for the challenge.
A virtual machine that contains all the services. It is provided prior to game start in a form of game image. Game image is identical for all teams.
A string that matches regex: /^\w{31}=$/.
A period of time for the checksystem to check and score all the teams. Game round usually takes about 1 minute.
A group of people that run the competition. Organizers do their best to provide a quality and fun event to all participants. Still organizers are to penalize/disqualify teams for rules violation and to solve the critical situations not described in these rules. Teams should be prepared to meet such decisions with understanding. Also organizers do determine the winner. In general, this decision is based on the scoreboard.
The competition begins when the organizers announce the decryption key for the game image. After that the game time is divided into two periods:
Key parameters in the scoring system are SLA and FlagPoints. Their values are individual for each service of each team. Team score is calculated as the sum of the products of the corresponding SLA and FlagPoints of all team’s services.
SLA (team, service) is the fraction of the game time in which that service of that team was in the UP state. E.g. if the service was always UP, SLA would be 1. If 4 hours passed from the game start and the service was UP during the first hour and then was not UP for the rest 3 hours, SLA would be 0.25. At the beginning of the game all teams have SLA equal to 1.
FlagPoints (team, service) is the number that correlates with a team’s ‘understanding’ of the service. FlagPoints depend on the team attack capabilities (exploiting vulnerabilities against other teams) and defense capabilities (fixing vulnerabilities in their own service). At the beginning of the game all teams have equal FlagPoints, and FlagPoints are updated every game round. If during the round the team failed both in attack and defense of the service, the corresponding FlagPoints will decrease, but will never reach 0. If during the round, the team was only able to defend the service, the corresponding FlagPoints will not change. If the team was able both to attack and to defend, the corresponding FlagPoints will grow.
Flag price is the number of FlagPoints got by attackers for stealing the flag from the victim.
Flag lifetime is the amount of time during which the flag must be available in the service for the checksystem. Teams should steal the flag and post it to the checksystem until it is expired.
The maximum amount of points awarded/deducted for the flag is equal to the number of the participating teams.If a flag was stolen from a team that was higher on the scoreboard in the previous round, the team that has stolen the flag earns the maximum number of FlagPoints. If a flag was stolen from a team that was below your team on the scoreboard, the number of FlagPoints will decrease based on the difference in teams’ positions on the scoreboard, but will never go below 1.
FlagPoints for a flag are awarded when that flag expires. Teams are ranged by total score.
Apart from FlagPoints, SLA and total score, the scoreboard shows the state of each service. There are four possible states of a service:
During the game, scoreboard will be available at http://monitor.ctf.hitb.org/monitor
You must submit your flags to http://monitor.ctf.hitb.org/flags
Flag submission example:
$ curl -s -H 'X-Team-Token: your_secret_token' -X PUT -d '["PNFP4DKBOV6BTYL9YFGBQ9006582ADC=", "STH5LK9R9OMGXOV4E06YZD71F746F53=", "0I7DUCYPX8UB2HP6D6UGN86BA26F2FE=", "PTK3DAGZ6XU4LPETXJTN7CE30EC0B54="]' http://monitor.ctf.hitb.org/flags | json_pp
[
{
"msg" : "[PNFP4DKBOV6BTYL9YFGBQ9006582ADC=] Denied: no such flag",
"status" : false,
"flag" : "PNFP4DKBOV6BTYL9YFGBQ9006582ADC="
},
{
"msg" : "[STH5LK9R9OMGXOV4E06YZD71F746F53=] Denied: flag is your own",
"flag" : "STH5LK9R9OMGXOV4E06YZD71F746F53=",
"status" : false
},
{
"status" : false,
"flag" : "0I7DUCYPX8UB2HP6D6UGN86BA26F2FE=",
"msg" : "[0I7DUCYPX8UB2HP6D6UGN86BA26F2FE=] Denied: you already submitted this flag"
},
{
"msg" : "[PTK3DAGZ6XU4LPETXJTN7CE30EC0B54=] Accepted. 1.73205080756888 flag points",
"flag" : "PTK3DAGZ6XU4LPETXJTN7CE30EC0B54=",
"status" : true
}
]
CTF Orga: ctf@hitb.org
Pre-CTF Training: ctf-training@hitb.org
CTF Discord Channel: https://discord.gg/3UCQf82